FluBot malware poses as Flash Player app
FinalSite ransomware attack shuts down thousands of school websites


Night Sky is the latest ransomware targeting corporate networks
It’s a new year, and with it comes a new ransomware to keep an eye on called ‘Night Sky’ that targets corporate networks and steals data in double-extortion attacks.
One of the victims has received an initial ransom demand of $800,000 to obtain a decryptor and for stolen data not to be published.
When launched, the ransomware will encrypt all files except those ending with the .dll or .exe file extensions. The ransomware will also not encrypt files or folders in the list below:
AppData
Boot
Windows
Windows.old
Tor Browser
Internet Explorer
Google
Opera
Opera Software
Mozilla
Mozilla Firefox
$Recycle.Bin
ProgramData
All Users
autorun.inf
boot.ini
bootfont.bin
bootsect.bak
bootmgr
bootmgr.efi
bootmgfw.efi
desktop.ini
iconcache.db
ntldr
ntuser.dat
ntuser.dat.log
ntuser.ini
thumbs.db
Program Files
Program Files (x86)
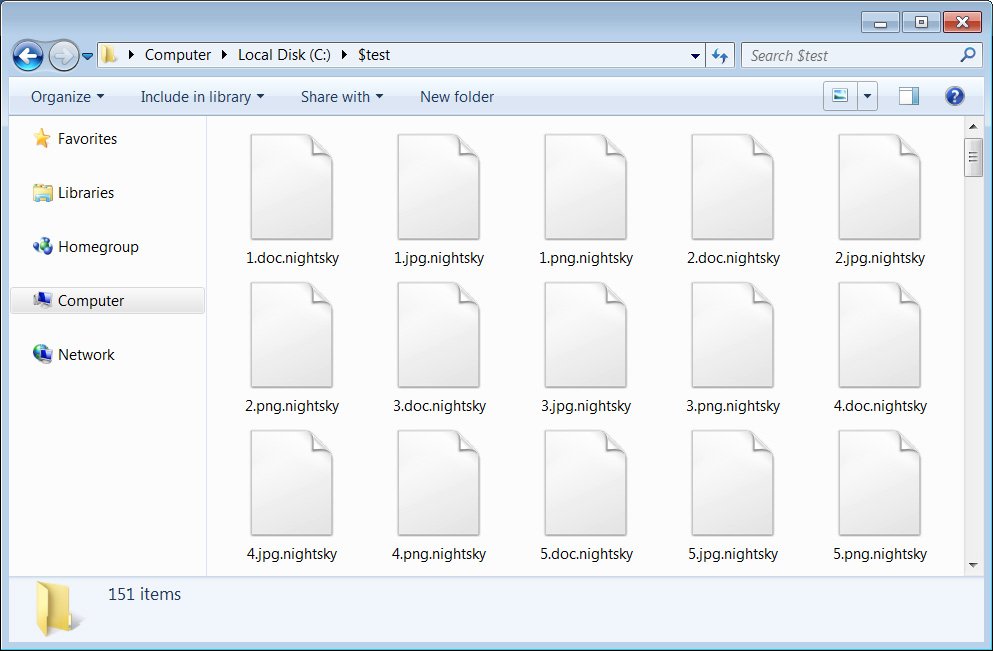
#recycleWhen encrypting files, Night Sky will append the .nightsky extension to encrypted file names, as shown in the image below.
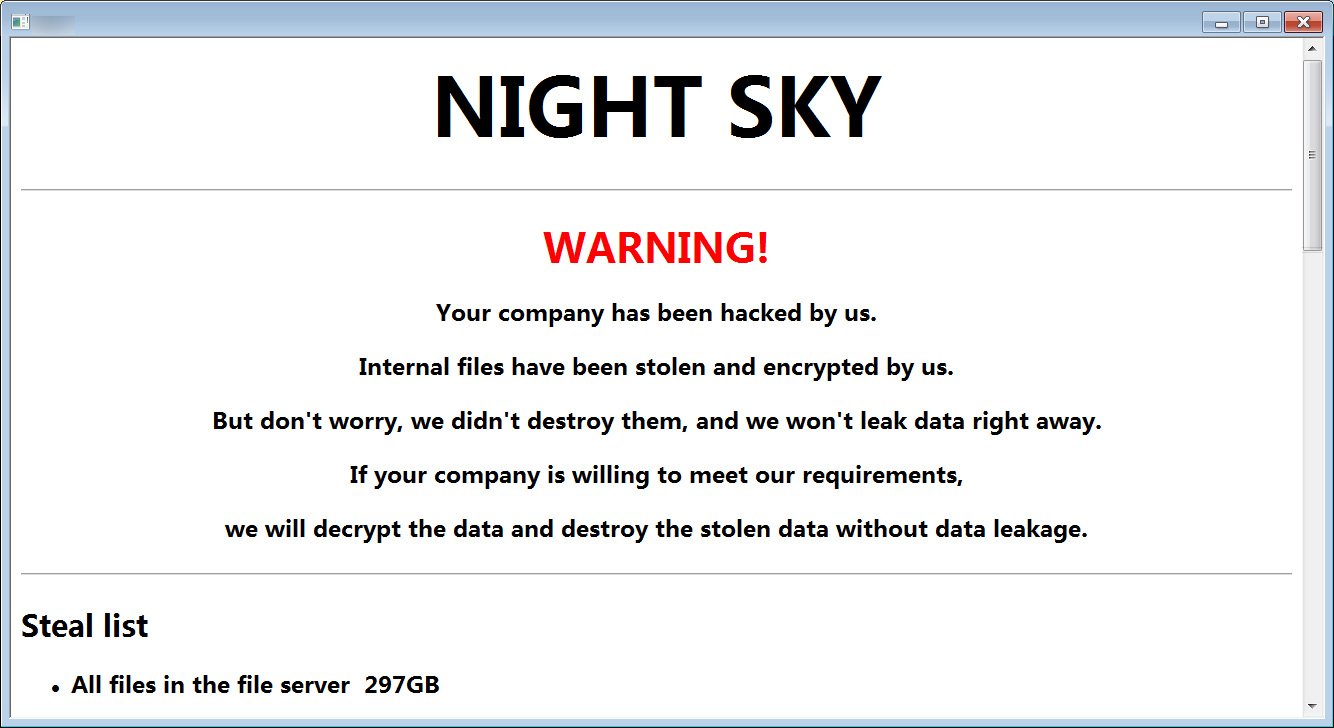
Instead of using a Tor site to communicate with victims, Night Sky uses email addresses and a clear web website running Rocket.Chat. The credentials are used to log in to the Rocket.Chat URL provided in the ransom note.
Double-extortion tactic
A common tactic used by ransomware operations is to steal unencrypted data from victims before encrypting devices on the network.
The threat actors then use this stolen data in a “double-extortion” strategy, where they threaten to leak the data if a ransom is not paid.
To leak victim’s data, Night Sky has created a Tor data leak site that currently includes two victims, one from Bangladesh and another from Japan.
Click for more about our Virus Removal Services
